Hub Authentication & Security: Understanding Web3Auth
Introduction
Web3Auth is an innovative solution designed to authenticate Web3 wallets, one of several aiming to create a safe, decentralized Internet of the future. It proposes a novel approach to manage crypto wallets: placing user security, privacy, and ease of use at the forefront, while adhering strictly to the key principles of Web3, such as user-centric control and decentralization.
Web3Auth is the current authentication solution we are currently using for the LAMINA1 Hub. Read below for an overview of how it works.
Web3Auth Explained
As an open-source, decentralized authentication protocol, Web3Auth leverages the power of blockchain technology to bridge the gap between Web2 and Web3 ecosystems. It allows users to interact securely with decentralized applications (dApps) by signing and verifying transactions with their private keys, which always remain under their control.
Web3Auth departs from traditional password-based systems, thus eliminating the associated security risks like phishing attacks and password theft. Instead, it uses cryptographic proofs, offering robust security and privacy guarantees. Importantly, users' data is encrypted and stored on their devices, not on a centralized server, establishing an extra layer of security and privacy.
Below are some of the advantages of using Web3Auth:
- Hassle-free Data Management: Users can manage sensitive data flows, encrypt sensitive data, and easily set up for GDPR, CCPA, CPRA compliance.
- Seamless Onboarding: Social login flows are indistinguishable from Web2.0 logins, contributing to greatly improved user experience and onboarding.
- Non-custodial Public Key Infrastructure: The user controls ownership and access to their cryptographic key pair. Login services only ever have access to one share; thus, it's impossible for the provider to retrieve the user's private key on their own.
User Flow
When researching and designing the LAMINA1 Betanet architecture, we ultimately concluded that the most effective approach for onboarding was to offer users three possible options for signing up or logging on to the LAMINA1 Hub:
- Social Login (OAuth): Utilizing an existing Discord, Google, or Twitter account
- Passwordless Email: Receiving a one-time code via your email for login
- External Wallet: Using your Metamask wallet/account
This method provides users with a familiar and user-friendly Web2 authentication experience. Importantly, it doesn't compromise the decentralization and censorship resistance principles inherent in a non-custodial environment, courtesy of Web3Auth's integration.
Based on user feedback, secure key management poses a significant challenge during the onboarding process for Web3 applications. However, with the Web3Auth modal, users are presented with the opportunity to dictate one of two preferred options for managing the authentication process.
Option 1: Trusting in an External Wallet, which allows users to sign and submit transactions while interacting with the blockchain through their platform. In this scenario, the management of your keys is reliant on their security measures.
Option 2: Trusting in OpenLogin technology, selected by us for its exceptional blend of user experience and security, creating what is currently recognized as multi-party computation (MPC) wallets.
While Option 1 is a more conventional and recognized process in this field, our focus will be on Option 2, which truly introduces innovative elements to the procedure.
Once the user starts the OpenLogin process:
- User is redirected to OpenLogin portal (app.openlogin.com), which handles the initial process of login
- User is redirected to login/OAuth provider (Google, Discord, Twitter, etc…) and carries out the authentication process with their preferred auth provider
- Users are then prompted to decide if they want to set up MFA on their OpenLogin account (Note: This option is prompted on every login until MFA is setup)
- If the user enables MFA, their secret key is then split into 3 shares, by default, as explained in the ‘Key Management’ section below.
- If they do not, their secret key is only split amongst the Web3Auth Auth Network, and their login will rely on them having access to that same OpenLogin account to retrieve the key upon consensus.
- User is redirected back to the portal, which then handles the reconstruction of the user’s key
- Finally, once the user is successfully authenticated, they are redirected back to application, with a derived key specific to the application/wallet.
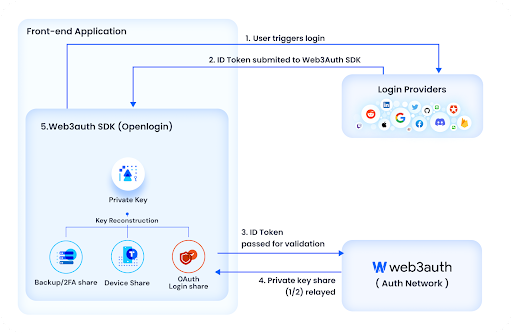
Note, per Step 5, that OpenLogin is considered an application wallet. Application wallets are wallets which are scoped specifically to dApps. This means that if you are logging in with the same application wallet on different applications, you will get different wallets (private keys).
On the other hand, external wallets are global for all applications. No matter where you are logging in, you will get the same keys if the same credentials are being provided. An example of an external wallet we are providing as a possible login option is the Metamask wallet.
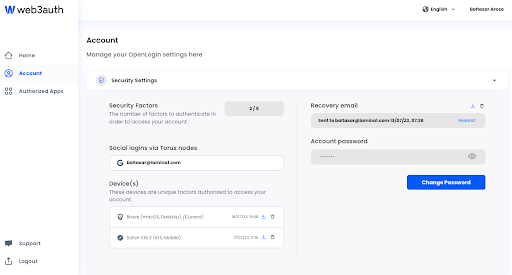
OpenLogin Portal
The image below depicts a screenshot of an account login on the OpenLogin Portal. As can be observed, this account maintains the default threshold of shares (2) but has increased the number of split shares to 5 by adding an additional device (Safari on iOS, Mobile) and establishing a 'master' password for the account.
This helps make their login more secure.
Key Management
The prevailing standard for Web3 key management today involves seed phrases –– sets of 12 or 24 words representing keys, which can be written down or stored in various ways. While this approach is technically straightforward, it's far from flawless. UX studies show that new users typically spend between 10-15 minutes onboarding into any new application, that losses due to misplaced or compromised seed phrases are common, and that the current standard for login and authentication using these key phrases is wanting in many aspects.
With Web3Auth, users handle keys similar to a multi-factor account, where they use their OAuth login, devices and other factors to manage their key pairs. In this example, the user begins by generating a 2 out of 3 (2/3) Shamir Secret Sharing. This gives the user three shares: ShareA, ShareB, and ShareC.
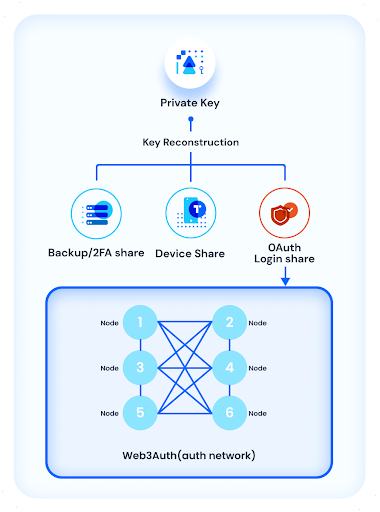
ShareA is stored on the user's device: Implementation is device and system specific. For example, on mobile devices, the share could be stored in device storage secured via biometrics.
ShareB is managed by a login service via node operators: This share is further split amongst a network of nodes and retrieved via conventional authentication flows.
ShareC is a recovery share: An extra share to be kept by the user, possibly kept on a separate device, downloaded or based on user input with enough entropy (eg. password, security questions, hardware device etc.). This information is conveyed in the form of a mnemonic, which can be dispatched to the user's email, if they so choose.
Similar to existing 2FA systems, a user needs to prove ownership of at least 2 out of 3 (2/3) shares, in order to retrieve his private key. This initial setup provides several benefits.
Using Web3Auth, the user is always in control of ownership and access to their cryptographic key pair. Login services only ever have access to one share, and thus it's not possible for the provider to retrieve the user's private key on their own.
Further, to create a social login share, a user has to use the Web3Auth Auth Network, where the key generation happens through a 5/9 consensus mechanism. This ensures that the keys are always non custodial to Web3Auth, social login Providers or any other party holding a key share.
Using the concept of Threshold Cryptography (with Shamir Secret Sharing), users only need a minimum of 2 out of nth number of key shares to get back their private key. This allows users to have control over their key and at the same time prevent account loss from a single point of failure (ie, they can lose their device and still have access to their account).
Conclusion
Web3Auth presents a significant breakthrough in the authentication methods for Web3 wallets. By replacing antiquated, insecure username/password combinations with decentralized, cryptographic proofs, it is making Web3 interactions safer and easier than ever before.
In a landscape where security and user-friendliness are often at odds, Web3Auth stands as a beacon, demonstrating that it is indeed possible to create systems that are both secure and easy to use.